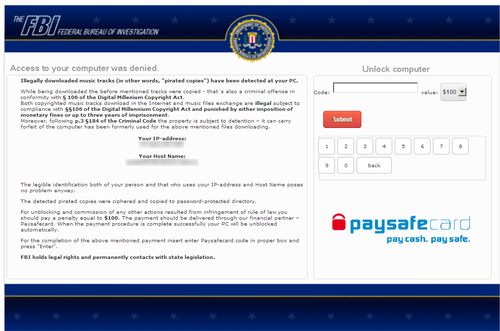
About 3 months ago I published an article regarding the ‘browlock’ browser ransomware here. Recently I discovered a new variant of this browser ransomware. This time in stead of a generic allegation from the local police department users are now warned because of piracy.
The first time this one popped up was around the end of September, at the time it was hosted on 213.133.111.10 (malwr.com). Currently it is hosted on 178.254.44.45 (malwr.com).

Different variations of this browserlocker 'scan’ the computer and find illegally downloaded music before redirecting to the locker page asking for a fine to be paid. The German variant seen:



After this the user is redirected to the gate of the browserlocker:
/panel/landing/gate.php?hwid=%
The % is filled with some ID generated from system metadata. This page then redirects the user to the correct country based template for the locker. These are titled, DE.php, NL.php, CH.php, etc. For this they use the Skypex Geo library.
This browserlocker variant should not even be called a browser locker as it doesn’t lock the browser at all. There is only some JavaScript to disable the right click option on the webpage. From the landing page:
<!–
//Disable right click script
function clickIE() {if (document.all) {(message);return false;}}
function clickNS(e) {if
(document.layers||(document.getElementById&&!document.all)) {
if (e.which==2||e.which==3) {(message);return false;}}}
if (document.layers)
{document.captureEvents(Event.MOUSEDOWN);document.onmousedown=clickNS;}
else{document.onmouseup=clickNS;document.oncontextmenu=clickIE;}
document.oncontextmenu=new Function(“return false”)
// –>
In no way does the landing page block the user from leaving and/or just closing the browser/tab like the first browlock did. The landing page itself looks ripped from other templates and the payment buttons sometimes intersects with the rest of the info.
The payment method is always Paysafecard, no other payment methods have been implemented by the actors at this time. There are however hints that they had implemented / are going to implement Ukash at some point, a snippet of JavaScript code in one of the landing page files:
$(function(){
var $write = $(’#ukashcode’),
shift = false,
capslock = false;
The panel from which they operate this scam also has partial broken scripts, references to scripts and stylesheets and more. For those wanting to poke around, the panel logins are located here:
178.254.44.45/loader/
178.254.44.45/panel/
178.254.44.45/panel2/
The actors behind this setup seem to originate from a German speaking country. This because the base template for their locker is German and their management panel as well. This can also be seen in their logout message:
178.254.44.45/loader/logout
This says “Logout erfolgreich!” which means logout was successful.
They currently target the following countries with their browser 'locker’:
- Austria
- Belgium
- Switzerland
- Germany
- Spain
- Great Britain
- Greece
- Italy
- Netherlands
- Portugal
- Sweden
- United States
And the designs for each country, Belgium has two designs as there is a Flemish and French speaking part of the country.
Austria:

Belgium (France version):
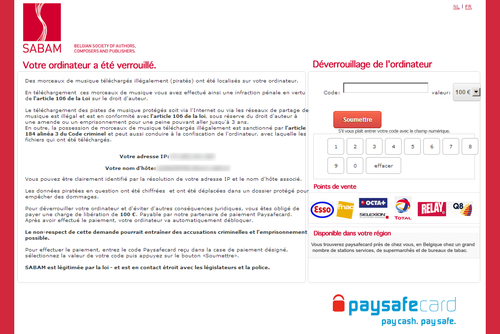
Belgium (Flemish version):
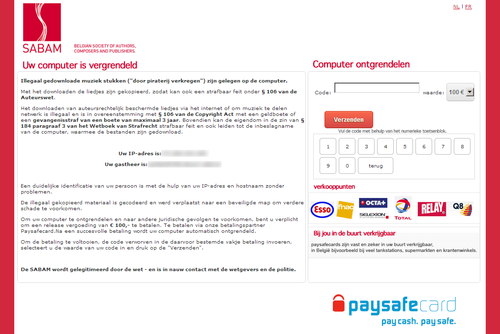
Switzerland:

Germany:

Spain:
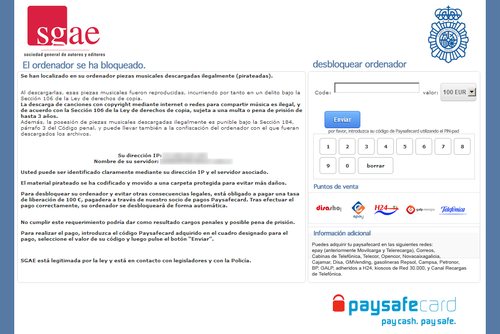
France:
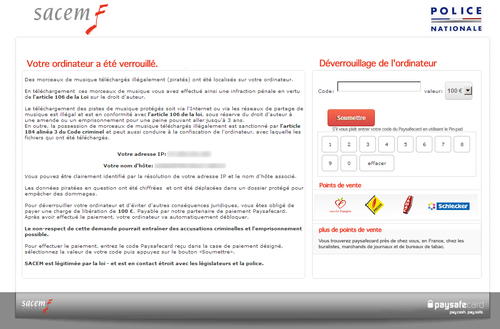
Great Britain:

Greece:

Italy:
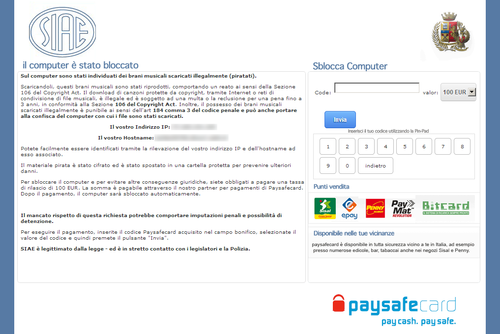
Netherlands:

Portugal:
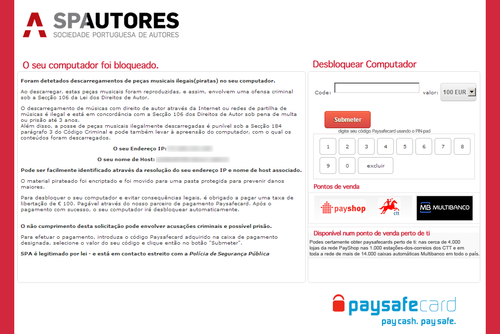
Sweden:
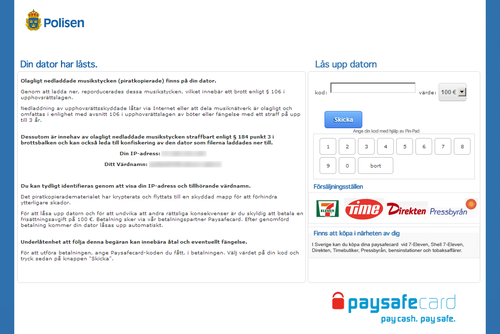
United States: