After finding the Neutrino exploit kit implemented CVE-2013-2551 around the 10th of September I noticed a couple of days ago Fiesta also started to serve this exploit. This blog entry is a general writeup about the Fiesta exploit kit and shows CVE-2013-2551 to exploit MSIE 6 through 10 as an example.
One thing to note about Fiesta is the way it serves exploits. It checks browser / plugin versions and determines to which exploit these are vulnerable and serves all of them. This means going to a Fiesta landing page with multiple vulnerable products leads to the client receiving exploits for all of these.
I got a hit in my VM for Fiesta trying to exploit my MSIE instead of the usual Java, PDF, Flash exploitation:
GET http://<domain> .tld/zxj3iyd/?2
200 OK (text/html) (VT: 0/48)
GET http://<domain> .tld/zxj3iyd/?2a59067246c00d795b045902020d030204530202045407090753010b53520e51
200 OK (text/html) (VT: 1/48)
GET http://<domain> .tld/zxj3iyd/?4579dd69c9446375514d5202565f020902070002500606020107030b07000f5a;1;3
200 OK (application/octet-stream) (VT: 22/48)
Looking at the initial landing page we get the usual obfuscated Javascript, while hiding its true purpose it is obvious to notice.
Looking at the correctly indented and formatted landing page you can spot a pattern used by the Javascript obfuscator used by the authors of this exploit kit. You see recurring patterns looking like this:
y = ‘iD3DPOO8’;
x = 22;
i = hoy(y, x);
u = 'iP0ZP6hDrj4bDReNO8rrj157bR’;
a = 22;
p = hoy(u, a);
This pattern is the result of a method of Javascript to index the properties of an object. Normal requests like these would look like 'somestring.length’ but in this case they would get the property value as 'somestring['length’]’. The obfuscated strings here, indicated by the var’s y and u are these strings to get the properties of an object. These strings are decrypted using an equally as obfuscated function. Here’s my rewritten version of the string decrypter:
The key used in this example was taking from the landing page my VM received (from the screenshot). Now if we pass the values from before through this function we get:
decrypt(’iD3DPOO8’,22); ==> “body”
decrypt(’iP0ZP6hDrj4bDReNO8rrj157bR’,22); ==> “createElement”
This pattern of obfuscation goes on throughout the whole page. After cleaning up these encrypted strings and the general layout of the code you will end up with something similar like this:
From this we can determin Fiesta currently targets:
- Java
- Java SE 7 Update 2 and earlier, 6 Update 30 and earlier, and 5.0 Update 33 and earlier CVE-2012-0507
- Java SE 7 Update 21 and earlier, 6 Update 45 and earlier, and 5.0 Update 45 and earlier CVE-2013-2463
- Java SE 7 Update 15 and earlier, 6 Update 41 and earlier, and 5.0 Update 40 and earlier CVE-2013-1493
- Microsoft Internet Explorer
- Microsoft Internet Explorer 6 through 10 CVE-2013-2551
- Adobe Flash
- Adobe Flash Player before 10.3.183.51 and 11.x before 11.5.502.149 CVE-2013-0634
- Adobe PDF
- Adobe Reader and Acrobat 8.x before 8.3, 9.x before 9.4.5, and 10.x before 10.1 CVE-2011-2104
The interesting part here is the Internet Explorer exploit which I saw the Neutrino exploit kit implement earlier. If we look at the deobfuscated exploit we can clearly see CVE-2013-2551 having been implemented by the authors of Fiesta:
If you want to read exactly how this exploit works I suggest you read the excellent article by the original team that discovered it, VUPEN, read their article here: Advanced Exploitation of Internet Explorer 10 / Windows 8 Overflow (Pwn2Own 2013)
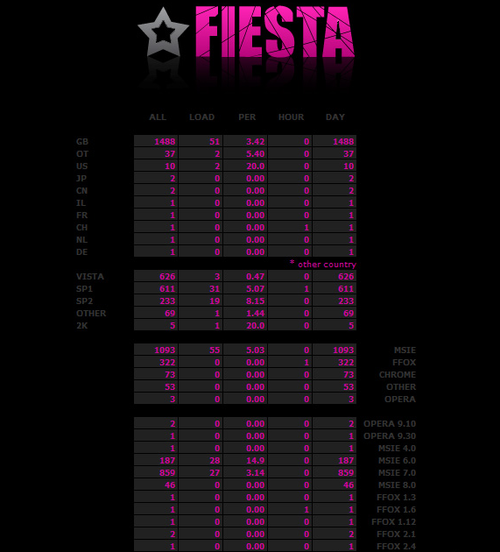
Personally I do not see the Fiesta exploit kit that often, this might be me looking in the wrong places or I’m not in the targeted countries. From what I can tell from the panel Fiesta is quite a simple setup but this could be wrong, the interface doesn’t say much about the whole back-end. Would you rent the Fiesta exploit kit your panel looks something like this (original image from abuse.ch):